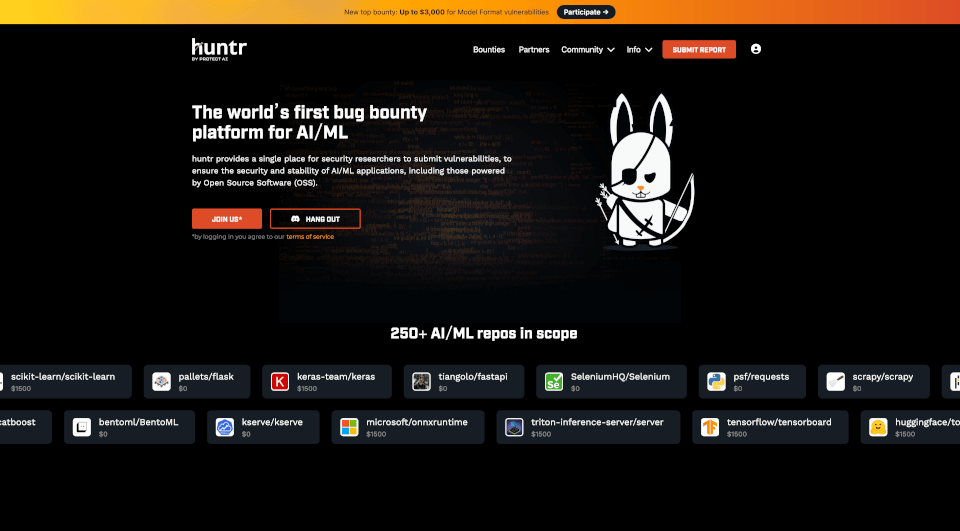
What is huntr?
Huntr is the world's first dedicated bug bounty platform specifically designed for AI and Machine Learning applications. As the tech landscape continuously evolves, the security of AI/ML systems has never been more crucial. Huntr aims to bridge the gap between innovative AI technologies and robust security measures, allowing security researchers to submit vulnerabilities to ensure the ongoing safety and reliability of AI/ML solutions, including those that leverage Open Source Software (OSS).
What are the features of huntr?
- Vulnerability Submission: Researchers can easily submit vulnerabilities through a secure and user-friendly interface, promoting swift action on identified issues.
- Bounty Rewards: Huntr offers competitive bounties for validated vulnerabilities, with rewards of up to $3,000 for specific security flaws such as Model Format vulnerabilities.
- Robust Tracking System: With an automated process, Huntr ensures that maintainers and researchers receive timely updates and follow-ups on submitted reports.
- Community Engagement: By joining Huntr, security enthusiasts can connect with like-minded professionals, share insights, and participate in growing a collective knowledge base around AI security.
- Diverse Repository Access: More than 250 AI/ML repositories are in scope, ensuring a wide range of software, including major frameworks like TensorFlow, PyTorch, and Hugging Face Transformers, are rigorously tested.
What are the characteristics of huntr?
- Security-Centric Approach: Focused on AI/ML, Huntr's primary goal is to identify and remediate vulnerabilities unique to this evolving domain.
- Dual-Track Validation: Once a vulnerability is reported, it undergoes a validation process involving both the Huntr team and software maintainers.
- Flexible Reporting: The platform allows maintainers to manage vulnerability reports effectively, giving them a window of 31 days to respond to findings.
- CVE Issuance: Validated reports result in the issuance of a CVE (Common Vulnerabilities and Exposures) for transparent public accountability.
- Transparent Publication: Reports are made public after 90 days by default, ensuring that information on vulnerabilities is available for educational and preventive purposes.
What are the use cases of huntr?
Huntr is invaluable in various application scenarios, promoting enhanced security practices. Some key areas include:
- Open Source Software Security: As many AI/ML applications rely on OSS, Huntr helps ensure that these widely-used libraries are free from vulnerabilities that could affect countless users.
- Research and Development: Organizations involved in R&D can benefit from Huntr by identifying weaknesses early in the development process, before deployment to production environments.
- Industry Compliance: For corporations seeking to comply with data protection regulations and cybersecurity standards, Huntr can assist in identifying vulnerabilities in their AI/ML systems.
- Educational Institutions: Universities and research institutions can utilize Huntr as a learning tool for students studying cybersecurity and machine learning, allowing them to engage with real-world vulnerabilities.
- Enterprise Deployment: Businesses deploying AI/ML solutions can leverage Huntr to audit existing applications, ensuring they uphold the highest security standards while innovating new products and services.
How to use huntr?
To start using Huntr, simply follow these steps:
- Register an Account: Sign up on the Huntr platform, agreeing to the terms of service.
- Explore Scope: Familiarize yourself with the list of AI/ML repositories eligible for bounties.
- Research and Identify: As a security researcher, identify potential vulnerabilities in those repositories.
- Submit Your Findings: Use Huntr’s secure form to submit your vulnerability reports clearly and concisely.
- Engage in Community: Connect with other researchers, share findings, and stay updated on the latest cybersecurity trends related to AI/ML.
huntr Pricing Information:
Huntr provides generous bounty payments for valid vulnerabilities as follows:
- Top Bounty: Up to $3,000 based on the severity and impact of submitted vulnerabilities.
- Repository Specific Bounties: Starting from $0 up to $1,500 or more, depending on the respective repository and associated risks.