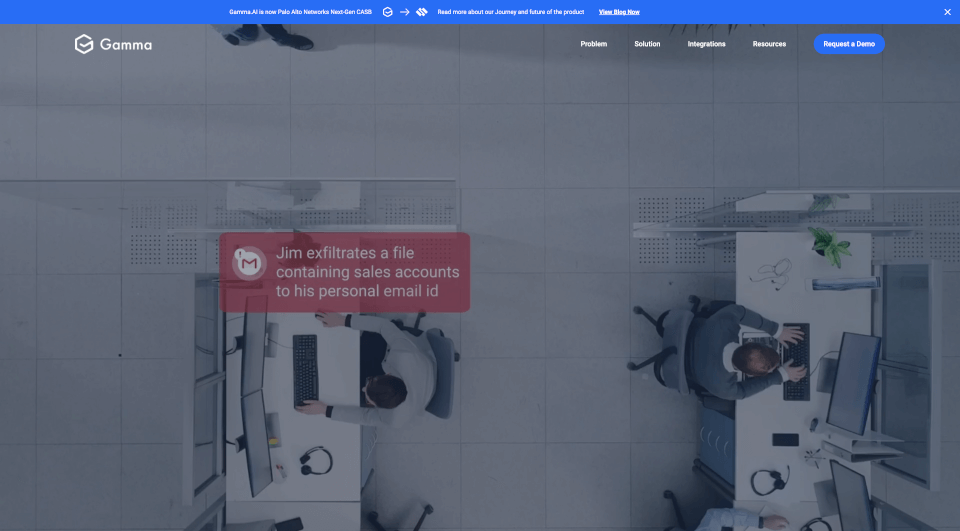
What is CrowdStrike?
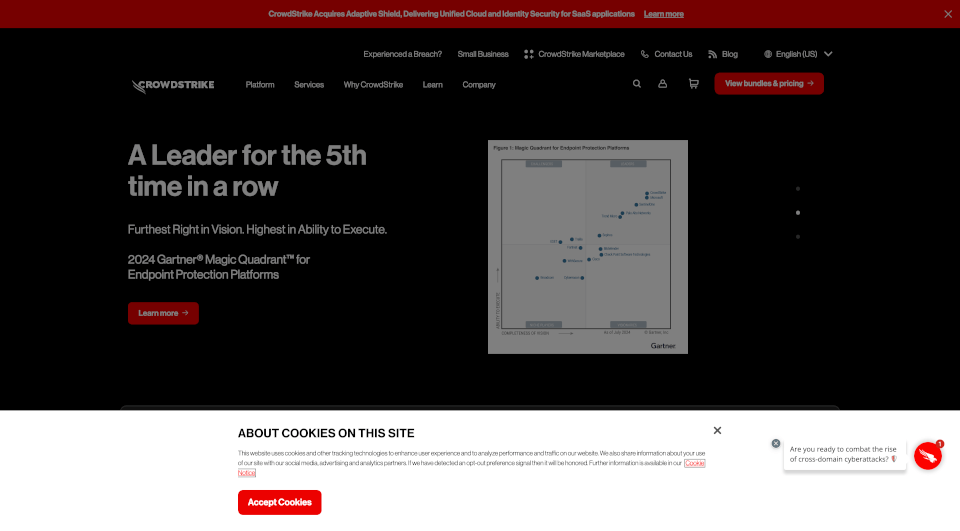
CrowdStrike is a global leader in cybersecurity, offering a cutting-edge cloud-native platform designed to protect endpoints, cloud workloads, identities, and data from advanced threats. With an AI-native approach to security, CrowdStrike has redefined how organizations guard against breaches and cyberattacks. Their modern solutions empower businesses to stay ahead of the evolving threat landscape, utilizing pioneering adversary intelligence to stop breaches before they occur.
What are the features of CrowdStrike?
Comprehensive Endpoint Protection: At the core of CrowdStrike's offerings is its advanced endpoint protection platform (EPP) and endpoint detection and response (EDR) technologies. These solutions leverage machine learning and behavioral analysis to proactively detect and mitigate threats in real-time.
AI-Native Architecture: The platform is built on an AI-native architecture, which allows for faster and more precise threat detection. This capability not only enhances security but also optimizes resource allocation, making it ideal for organizations of all sizes.
Unified Security Management: CrowdStrike provides a unified security solution that integrates identity protection, cloud security, and data protection. This holistic approach simplifies security management, allowing teams to address multiple aspects of cybersecurity from a single console.
Generative AI Workflows: The introduction of generative AI workflows revolutionizes cybersecurity operations, enabling teams to automate and streamline processes. By turning hours of work into minutes, organizations can focus more on strategic tasks rather than mundane routines.
Threat Intelligence and Hunting: With world-class cyber threat intelligence and elite threat hunting capabilities, CrowdStrike is equipped to deliver proactive threat assessments and interactively disrupt potential adversaries.
SaaS and Cloud Security Solutions: As more organizations gravitate towards cloud-based applications, CrowdStrike offers tailored solutions for securing software-as-a-service (SaaS) applications, ensuring a comprehensive protective umbrella across various deployment scenarios.
What are the characteristics of CrowdStrike?
- Real-time Detection and Response: The platform's ability to provide real-time visibility and response capabilities allows organizations to quickly react to threats as they arise.
- Scalability: Whether it’s a small business or a large enterprise, CrowdStrike’s platform can scale to meet the specific needs of any organization.
- User-Friendly Interface: The user interface is designed for ease of use, making it accessible for security teams of all skill levels to navigate and utilize effectively.
- Multi-Platform Support: CrowdStrike supports a variety of operating systems and devices, ensuring comprehensive coverage across diverse IT environments.
- Integration Capabilities: Seamless integration with existing IT and security tools enables a smoother implementation process and enhances overall security posture.
What are the use cases of CrowdStrike?
CrowdStrike’s cybersecurity solutions are suited for a variety of sectors facing differing threats:
Small Businesses: Tailored solutions help small businesses safeguard their digital assets with robust protection without breaking the bank.
Healthcare: Given the sensitive nature of patient data, healthcare organizations can protect against data breaches while ensuring compliance with regulations.
Government: Federal and state entities can leverage CrowdStrike to protect national security interests and sensitive information from adversarial attacks.
Retail: As the retail industry increasingly adopts digital transformation, CrowdStrike helps secure customer data and transaction processes from cyber threats.
Finance: By utilizing advanced threat intelligence, financial institutions can prevent fraud and protect customers from identity theft.
How to use CrowdStrike?
- Implementation: Begin by signing up for CrowdStrike services and receiving the necessary login credentials.
- Installation: Follow the installation guide provided to deploy the endpoint protection agent on your systems.
- Configuration: Set up the configuration settings according to your organization’s security needs and compliance requirements.
- Ongoing Management: Use the centralized dashboard to monitor security incidents, adjust policies, and manage alerts.
- Training: Attend CrowdStrike’s training sessions and workshops to maximize the effectiveness of your cybersecurity posture.